What honeypot can I deploy in less than 5 minutes
15 October 2023 | by Xavier Bellekens

In today’s dynamic digital landscape, the need to stay one step ahead of cyber adversaries is more pressing than ever. Amidst an arsenal of cybersecurity tools, honeypots emerge as an intriguing and often underutilized defense mechanism
In this blogpost, we’re going to delve deeper into the nuanced world of honeypots and provide a guide on swiftly setting one up for your enterprise in the cloud.
Demystifying the Honeypot
A honeypot can be best described as a cybersecurity sentinel. It’s essentially a decoy – a system or application intentionally configured to mimic the attributes of genuine IT assets. Its primary job isn’t to fend off attackers, but to attract and ensnare them. Picture it as a mock bank vault left deliberately vulnerable; its sole purpose is to lure in and trap thieves, all while keeping the real vault safe and untouched.
The Magic of High Alert Fidelity
When we talk about the unparalleled strengths of honeypots, high alert fidelity tops the list. In the realm of cybersecurity, sifting through alerts to determine their legitimacy can often feel overwhelming. Many security mechanisms generate a flood of alerts, some genuine and others mere distractions.
This is where the beauty of honeypots shines through. Given their nature, any interaction with a honeypot is almost always suspicious. After all, there’s no legitimate reason for someone to interact with a decoy. Consequently, alerts stemming from honeypots carry a high degree of authenticity. The likelihood of a false positive – an alert indicating a threat when there isn’t one – is significantly reduced.
The Underestimated Efficacy of Honeypots
While the concept of honeypots has been around for a while, they often fly under the radar in many cybersecurity strategies. This oversight can be attributed to a few reasons:
- Complexity Misconception: Many erroneously believe that deploying and managing honeypots is a complex task, reserved only for large organizations with extensive resources.
- Lack of Awareness: Simply put, not everyone is aware of the remarkable benefits honeypots bring to the table in terms of threat intelligence and alert fidelity.
Yet, those who have embraced honeypots often attest to their value. They not only provide a fascinating insight into the methods and motives of attackers, but also significantly refine the alerting process, ensuring that the security teams’ focus remains undivided and precise.
Snare: Best All-in-One Deception as a Service Solution
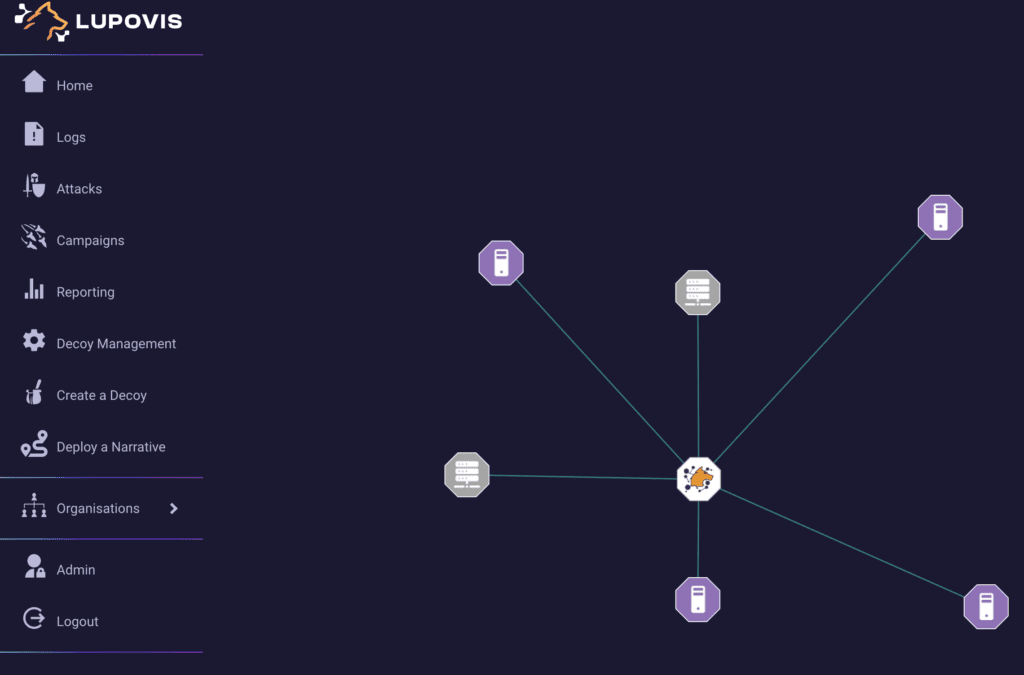
If you’re in the market for a top-tier enterprise honeypot solution, look no further than Snare. Boasting an array of features tailored for advanced threat detection, Snare stands out with its intuitive interface, a comprehensive library of threat signatures, and state-of-the-art deception techniques. Given that Snare is designed with user-friendliness in mind, it shines as the ultimate honeypot solution even for those relatively new to the cybersecurity landscape.
Furthermore, Snare seamlessly integrates with an array of other SIEM tools and other platforms, ensuring that your defense mechanisms are both robust and interconnected.
According to a SOC Manager for an MSSP, Snare is a powerhouse in the honeypot arena. “Snare is more than just a honeypot; it’s a holistic solution,” she opines. “Being a part of a larger cybersecurity ecosystem, it not only detects threats but provides unparalleled insights. This integrated approach ensures that our security posture is always a step ahead, enabling proactive threat mitigation across all fronts.”
Snare Core Functionalities
- Contextual threat intelligence
- 0 false positive
- Quick and Hassle Free (5 minutes) deployment
- Global threat intelligence API included
- Ability to identify pre-breach events
- Fully integrated Dashboard
Snare Pros
- Seamless integration with all major SIEMs
- Healthy selection of deceptive templates
- Identify humans and bots
- 30 days free trial
Snare Pros
- If you opt for a premium plan, it may be more costly than other options listed
- Rich functionality may be under-utilized by beginners
T-Pot: Leading Open-Source Honeypot Solution for Comprehensive Threat Detection
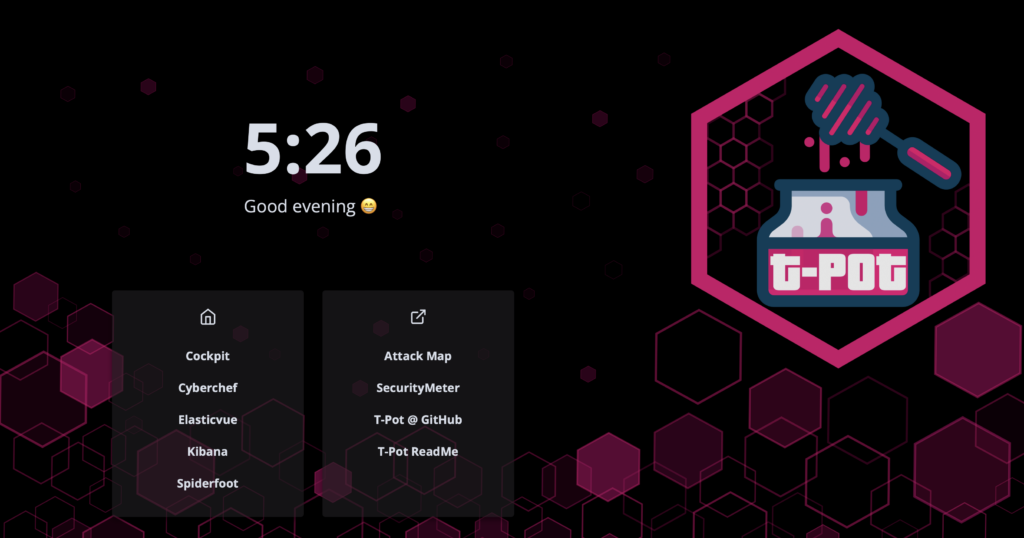
For organizations looking to adopt a cost-effective honeypot solution, T-Pot is an undeniable frontrunner. Originating from the open-source community, T-Pot offers a plethora of features specially curated for efficient threat detection. Its standout features include a user-friendly dashboard, a wide range of sensor integrations, and cutting-edge deception methodologies. What makes T-Pot especially appealing is its commitment to making cybersecurity accessible, allowing even novices to harness its capabilities effortlessly.
T-Pot Core Functionalities
- Multi-Honeypot Integration
- Comprehensive Visualization Dashboard
- Automated Data Parsing
- Elasticsearch Backend
- Diverse Sensor Deployment
T-Pot Pros
- Open-Source Nature
- Active Community
- Modular Design
T-Pot Cons
- Steep Learning Curve
- Community-Driven Support
- Resource Requirements
- Scalability And Maintenance are difficult
Cowrie: Premier SSH and Telnet Honeypot for In-Depth Threat Analysis

Organizations aiming to bolster their defenses against SSH and Telnet-based attacks should look no further than Cowrie. Born from the open-source community, Cowrie has rapidly grown in stature, being recognized for its intricate logging capabilities and the depth of interaction it offers to potential attackers. Designed with realism in mind, Cowrie doesn’t just identify intrusion attempts; it immerses attackers in a fabricated environment, logging their every move.
Moreover, Cowrie is tailored to integrate effortlessly with threat intelligence platforms and SIEM systems, rendering it a perfect fit for organizations aiming for a synergistic security setup.
A Lead Security Researcher from a notable cybersecurity institute comments, “Cowrie serves as a revelation in the world of SSH and Telnet honeypots. Its depth of interaction ensures we gain invaluable insights into attacker methodologies. This isn’t just about detecting threats; it’s about understanding them.”
Cowrie Core Functionalities
- High Interaction Environment: Cowrie offers a simulated environment, leading attackers to believe they’re on a real system, hence logging deeper and more realistic interactions.
- Detailed Logging: Records exhaustive logs of sessions, including shell commands, file uploads, and attempted system modifications.
- Extensible and Modular: Supports the addition of plugins and custom functionalities to enhance its capabilities.
- Real-Time Alerts: Integrated mechanisms to provide real-time alerts on detected activities.
- Flexibility: Can be run as an SSH server and a Telnet server, or both simultaneously.
Cowrie Pros
- Deep Insights: By simulating a real system, Cowrie provides unparalleled depth into attacker tactics and behaviors.
- Open-Source Advantage: Free to deploy and benefits from regular community-driven enhancements.
- Integration-Friendly: Designed to work seamlessly with popular threat intelligence platforms and SIEM tools.
- Rich Dataset Generation: Ideal for researchers and analysts aiming to study attack patterns.
- Dynamic Configuration: Enables modifications on-the-fly without the need to restart the honeypot.
Cowrie Cons
- Setup Complexity: Might require a bit of a learning curve for those new to honeypots.
- Targeted Scope: While brilliant for SSH and Telnet, Cowrie is specialized and might not capture non-SSH/Telnet based threats.
- Maintenance: Being open-source, it relies on community or user-driven updates, and might not always be as up-to-date as commercial solutions.
Why is Deploying Honeypots Crucial for Your Enterprise?
Whether you’re initiating your cybersecurity measures or augmenting your existing defenses, the inclusion of honeypots can prove instrumental in enhancing your security posture. (Curious about their efficacy? We’ll dive deep.)
Without honeypots, you might be leaving your network exposed to unidentified threats. That’s why real-time threat detection, deception, and incident response are vital — and honeypots play a significant role in these areas.
Here’s why deploying honeypots is indispensable:
- Honeypots Act as an Early Warning System. The cyber realm is often the first battleground between your enterprise and potential threat actors. With honeypots, you can detect intrusion attempts early, buying invaluable time to mitigate potential risks. An undetected intrusion can cause significant damage to your enterprise, both in terms of data loss and reputation.
- Honeypots Enhance Threat Intelligence. Honeypots not only detect threats but also study attacker methodologies. The insights gathered can provide a deeper understanding of the current threat landscape, shaping your security strategies accordingly.
While one can gain knowledge on threat intelligence through extensive research, collaborating with a seasoned cybersecurity firm with honeypot expertise can provide specific insights tailored to your enterprise.
- Honeypots Reflect Your Commitment to Cybersecurity. By proactively deploying honeypots, it demonstrates to stakeholders, partners, and clients that you prioritize security. A robust security setup, evident through advanced measures like honeypots, can reinforce trust and emphasize your commitment to data protection.
Conversely, if minimal effort is invested in cybersecurity, stakeholders might question the overall dedication of your enterprise towards safeguarding critical data.
- Honeypots Build Confidence in Your Security Posture. A well-strategized honeypot deployment can bolster confidence in your cybersecurity measures. When threats are consistently detected and neutralized, it showcases the effectiveness of your security infrastructure.
By continually updating and refining your honeypot strategies, you can ensure that trust is maintained, paving the way for more meaningful engagements with clients and partners.
- Honeypots Ensure Dynamic Defense Adaptability. In the ever-evolving world of cyber threats, adaptability is key. Honeypots not only provide insights into current threats but can also be reconfigured to simulate diverse environments, ensuring that your defenses remain adaptable and relevant.
Given their significance, it might be beneficial to collaborate with a cybersecurity firm proficient in honeypot deployments, ensuring a robust and effective setup tailored for your enterprise.
Leverage Honeypots for a Fortified Cyber Defense The right honeypot setup can empower your enterprise to detect, deceive, and respond to threats with unparalleled efficacy. Fortunately, there are numerous solutions available, both open-source and commercial. Make it a priority to explore and integrate honeypots into your security framework, fortifying your defenses against ever-evolving cyber threats.
15 October 2023 | by Xavier Bellekens
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.


