The 13 Best SOC Analysts Resources and Tools
4 July 2023 | by Xavier Bellekens

Picture this: the cybersecurity world is like a rollercoaster, with threats coming at you from every angle. That’s where the rockstar Security Operations Center (SOC) analysts step in to save the day! They’re the superheroes defending organizations’ digital assets against the bad guys. But they don’t go into battle empty-handed. Oh no! They’ve got an arsenal of mighty tools and technologies at their disposal.
⬇️ Download NOW : SOC Transformational Guide
In this blog post, we’re diving deep into the SOC analyst’s toolkit to uncover the best weapons they use to tackle the ever-changing threat landscape. Get ready for a wild ride!
Note: there’s a mix of free and paid options that can suit your needs. It’s like a choose-your-own-adventure story, where some tools offer free plans with the option to upgrade, while others have paid plans with free options available. To find the perfect fit for your needs and goals, we recommend visiting the pricing pages of the tools you’re most interested in. That way, you can explore the features and benefits of each plan and make an informed decision that aligns with your requirements. Remember, it’s all about finding the right tool at the right price for you.
FREE TOOLS
While these tools are free to use, it’s worth noting that some offer paid options with extra features. Nonetheless, the free versions still provide substantial value. We’ve highlighted the standout features of each tool, enabling you to maximize their potential and enhance your efforts.
1. Lupovis Prowl
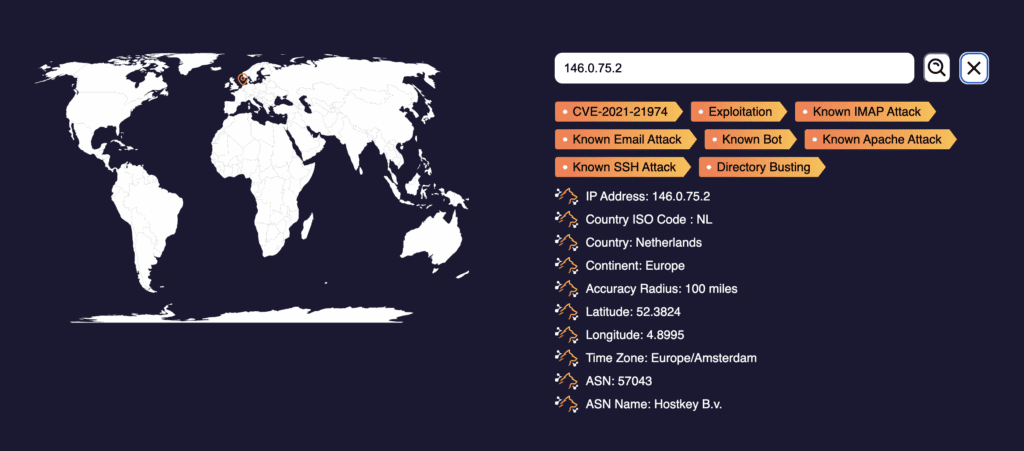
The goal of Prowl is to provide actionable intelligence and insights to cybersecurity professionals and organizations. Prowl collects and analyzes internet-wide scan and attack data, filtering out noise and false positives to focus on identifying legitimate and significant threats.
By offering this curated dataset, Prowl aims to help security teams prioritize and respond effectively to genuine threats, reducing the overall noise and improving the efficiency of cybersecurity operations.
Prowl has one of the largest IP database that leverage thousands of sensors around the world.
With the Lupovis Prowl Actionable Intelligence, you can:
- Identify Relevant Threats: Access a curated dataset of internet-wide scan and attack data to focus on real and significant threats, filtering out noise and false positives.
- Prioritize Incident Response: Gain actionable intelligence to prioritize incident response efforts based on the severity and relevance of detected threats. Learn how to integrate the API to Azure Sentinel.
- Reduce Alert Fatigue: Minimize false positives and unnecessary noise in your security monitoring by leveraging Prowl’s refined data, allowing your team to focus on genuine threats.
- Enhance Cybersecurity Operations: Improve the efficiency and effectiveness of your cybersecurity operations by leveraging the insights provided by Prowl to streamline threat analysis and response.
- Strengthen Defense Strategies: Utilize Prowl’s intelligence to better understand attacker behaviors and tactics, enabling you to fortify your defense strategies against emerging threats.
- Optimize Resource Allocation: Allocate your cybersecurity resources more effectively by concentrating efforts on genuine threats identified by Prowl, ensuring a more targeted and efficient response.
- Stay Proactive and Informed: Keep up with the evolving threat landscape and stay informed about emerging attack patterns and trends to proactively mitigate potential risks.
- Enhance Incident Investigation: Leverage Prowl’s extensive dataset to conduct detailed investigations and gain insights into the origin, frequency, and patterns of various scan and attack activities.
2. Process Hacker
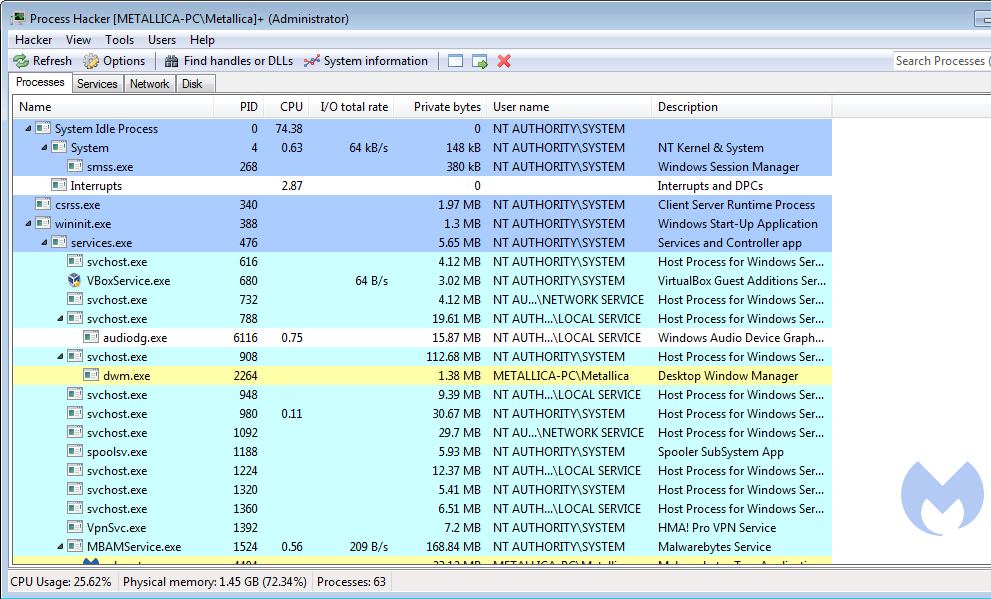
Process Hacker is a free and open-source process viewer and system monitoring tool for Windows operating systems. It provides advanced functionality for managing processes, monitoring system performance, and analyzing system internals.
Here are some key features of Process Hacker:
- Process Management: Process Hacker allows you to view and manage running processes on your system. You can terminate processes, suspend or resume their execution, and even set process priorities.
- System Monitoring: The tool provides real-time monitoring of system resources, such as CPU usage, memory usage, disk activity, and network activity. You can monitor individual processes or get an overview of system-wide performance.
- Process Details and Properties: Process Hacker provides detailed information about running processes, including file and folder details, network connections, loaded DLLs, and process privileges. You can also view and modify process properties.
- Process Tracing and Debugging: Process Hacker offers advanced debugging features, allowing you to trace system calls, monitor thread activity, and inspect memory usage. This makes it useful for troubleshooting and analyzing software behavior.
- System Services and Drivers: You can view and manage system services and drivers using Process Hacker. It provides an interface to start, stop, and modify properties of services and drivers installed on your system.
- Network Monitoring: Process Hacker includes network monitoring capabilities, allowing you to view active network connections, monitor network traffic, and inspect detailed information about each connection.
- Security Analysis: The tool provides features to analyze process and system security, such as checking for unsigned processes, identifying hidden processes, and detecting suspicious behavior.
3. BrowsingHistoryView
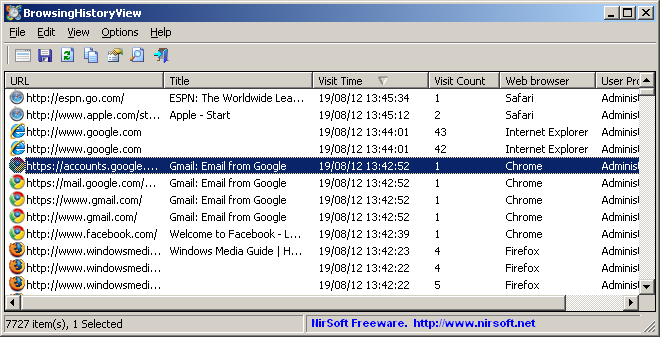
BrowsingHistoryView is a free utility that allows you to view and analyze the browsing history data from various web browsers installed on your Windows system. It provides a convenient way to explore your browsing activities and extract useful information for analysis or troubleshooting purposes.
Other ways that you can use BrowsingHistoryView is to understand the data stored by a user’s browser:
- Cross-Browser Support: BrowsingHistoryView supports a wide range of web browsers, including Internet Explorer, Mozilla Firefox, Google Chrome, Microsoft Edge, and Opera. It can retrieve and display browsing history data from these browsers in a unified interface.
- Detailed Browsing History Display: The tool presents the browsing history data in a comprehensive manner, showing details such as URL, title, visit time, visit count, and browser process ID. It also provides information about the browser profile and the user profile associated with each history entry.
- Filtering and Searching: BrowsingHistoryView offers powerful filtering and searching capabilities. You can filter the displayed history items based on specific criteria like time range, specific URLs or keywords, visit count, and more. This allows you to narrow down the history entries to find the information you need.
- Export and Save History Data: You can export selected history items or the entire browsing history to various formats, including HTML, XML, CSV, and text files. This feature enables you to save and analyze the history data using external tools or share it with others.
- Command-Line Support: BrowsingHistoryView includes command-line options, allowing you to automate the retrieval and analysis of browsing history data. This can be helpful for advanced users or for incorporating the tool into scripts or batch processes.
4. FullEventLogview
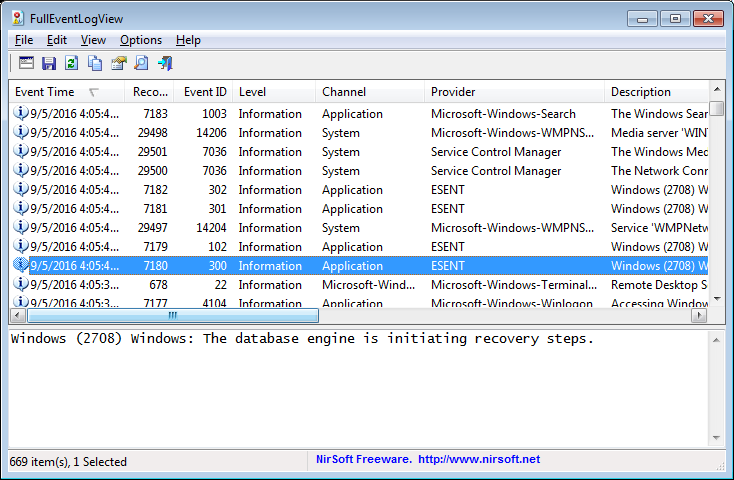
FullEventLogView is a free utility that allows you to view and analyze the Windows event logs stored on your system. It provides a comprehensive and user-friendly interface to explore event log entries, filter and search for specific events, and export the log data for further analysis.
Here are some key features of FullEventLogView:
- Event Log Viewer: FullEventLogView supports viewing and analyzing event logs from various sources, including the Application, Security, System, and other custom event logs created by Windows and installed applications.
- Rich Event Details: The tool displays detailed information about each event log entry, including the event ID, event source, event description, log time, log level, and more. This helps you understand the nature and context of the events recorded in the logs.
- Filtering and Searching: FullEventLogView allows you to apply filters and search for specific events based on various criteria, such as event type, event ID, log source, log time range, and event description. This makes it easier to narrow down and locate the events you are interested in.
- Custom Views and Exporting: You can create custom views to focus on specific events or event types within the log. The tool also enables you to export selected events or the entire log to various file formats, including HTML, XML, CSV, and text files. This enables further analysis or sharing of the log data with others.
- Command-Line Support: FullEventLogView provides command-line options, allowing you to automate log analysis tasks or incorporate the tool into scripts and batch processes. This can be particularly useful for advanced users or system administrators.
5. Virustotal

VirusTotal is a web-based service that allows users to scan files, URLs for potential malware or malicious activities. It aggregates multiple antivirus engines and other security tools to provide comprehensive results and insights into the scanned items.
You can leverage virustotal for file scanning and understanding what malware hides within the file.
- File Scanning: Users can upload files to VirusTotal for scanning, and the service checks the file against numerous antivirus engines and other security tools. The results provide information on whether any of the engines flagged the file as potentially malicious.
- URL Scanning: VirusTotal also analyzes URLs to determine if they are associated with any malicious activities or if they have been flagged by any security sources. This helps in assessing the safety of websites and detecting potential threats.
- Community Contributions: VirusTotal benefits from contributions by its user community, which helps in continuously improving the detection capabilities and accuracy of the service.
- Additional Tools: VirusTotal offers additional tools and features, such as the ability to search for previously scanned items, view historical data, and access detailed reports on scan results.
6. AbuseIPDB
AbuseIPDB is a free online service that provides a platform for reporting and tracking malicious IP addresses involved in various types of abusive activities, such as hacking attempts, brute-force attacks, and spamming. It allows users to report and search for IP addresses associated with abusive behavior, aiding in the identification and prevention of potential threats.
Here are some key features of AbuseIPDB:
- IP Address Reporting: Users can report IP addresses that have been involved in malicious activities, including hacking attempts, port scanning, or other abusive behaviors. Reports include details about the incident and can help warn others about potentially dangerous IP addresses.
- IP Address Lookup: AbuseIPDB allows users to search its database using IP addresses to determine if they have been reported for abusive activities. This can help identify suspicious or known malicious IP addresses and assist in making informed decisions regarding network security.
- Scoring System: AbuseIPDB utilizes a scoring system that rates the reputation of IP addresses based on the number of abuse reports received and the severity of the reported incidents. This scoring system helps in gauging the potential risk associated with an IP address.
- Community Collaboration: The service encourages community collaboration by allowing users to contribute reports and help in maintaining an extensive database of abusive IP addresses. This collaborative approach strengthens the effectiveness of AbuseIPDB as a resource for detecting and mitigating potential threats.
7. CISCO Talos
Cisco Talos offers a range of valuable features and services, including:
- Security Advisories: Talos publishes security advisories and alerts to keep organizations informed about critical vulnerabilities, patches, and recommended actions to strengthen their security posture.
- Reputation and IP Blacklisting: Talos maintains a database of known malicious IP addresses, domains, and URLs, providing reputation and blacklisting services to help organizations block access to potentially harmful sources.
- Incident Response Support: Talos offers incident response support to assist organizations in effectively managing and mitigating security incidents, minimizing their impact.
- Email and Web Security: Talos provides solutions and services to enhance email and web security, including threat detection, spam filtering, and protection against phishing attacks.
- Security Technology Development: Talos actively contributes to the development of security technologies and innovations, collaborating with industry partners and the open-source community.
- Threat Intelligence Feeds and APIs: Talos offers threat intelligence feeds and APIs, allowing organizations to integrate real-time threat data into their security solutions for faster detection and response.
8. AnyRun
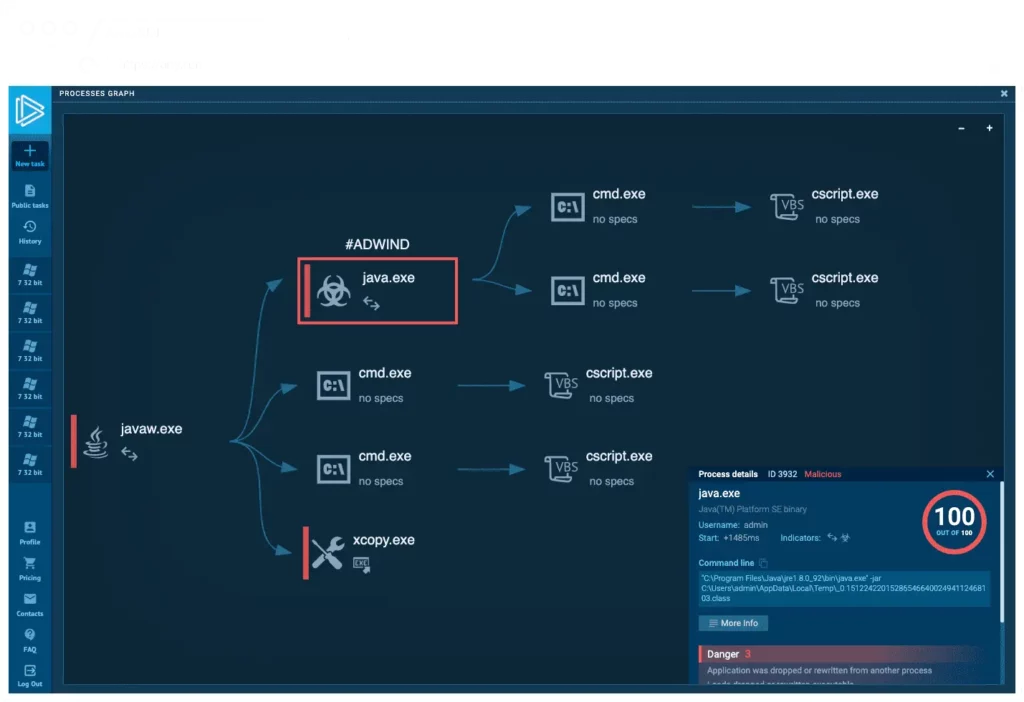
Any.Run is a popular online interactive malware analysis platform that allows users to safely execute and analyze potentially malicious files in a controlled environment. It provides a virtual sandbox where users can upload and execute suspicious files or URLs to observe their behavior and analyze their potential impact.
Here are some key features of Any.Run:
- Interactive Sandbox: Any.Run offers an interactive environment where users can execute files or URLs and observe their behavior in real-time. This helps users understand the actions and potential risks associated with the analyzed sample.
- Behavior Analysis: Any.Run provides detailed behavior analysis reports, allowing users to monitor the interactions between the analyzed file and the operating system. This includes information about registry modifications, network communications, and file system changes.
- Traffic Capture and Analysis: Any.Run captures and analyzes network traffic generated by the executed samples, providing insights into potential malicious connections, communication protocols, and data transfers.
- Visualized Process Tree: Any.Run presents a visual process tree that illustrates the relationships and dependencies between processes, helping users identify any suspicious or unexpected activities.
9. Hybrid Analysis

Hybrid Analysis is a powerful online platform that enables users to analyze and investigate suspicious files and URLs for potential malware and threats. It combines the capabilities of both static and dynamic analysis techniques to provide comprehensive insights into the behavior and impact of analyzed samples.
Here are some key features of Hybrid Analysis:
- File and URL Analysis: Hybrid Analysis allows users to upload files or submit URLs for analysis. It supports a wide range of file types, including executables, documents, scripts, and more. Users can also analyze websites and URLs to uncover potential threats or malicious activities.
- Static Analysis: Hybrid Analysis performs static analysis of the submitted samples, extracting valuable information such as file properties, strings, embedded resources, and potential indicators of compromise (IOCs). This helps in understanding the nature and characteristics of the analyzed samples.
- Dynamic Analysis: Hybrid Analysis executes the submitted samples in a controlled virtual environment, observing their behavior and interactions with the system. This includes monitoring network traffic, file system modifications, registry changes, and process activity. It provides detailed reports on the observed behavior, helping to identify potential malicious actions.
- Community Sandbox: Hybrid Analysis benefits from a collaborative community of users who contribute and share their analysis results. This fosters collective knowledge and enables users to benefit from insights and findings from other researchers and analysts.
9. Urlscan
URLScan is an online service that helps analyze and inspect the contents of a given URL or website. It provides detailed insights into the website’s structure, behavior, and potential security risks. By scanning URLs, users can gather valuable information for security analysis, threat detection, and investigation purposes.
Here are some key features of URLScan:
- URL Inspection: URLScan allows users to submit a URL for analysis and generates a detailed report on the website’s components, including its structure, headers, and resources.
- Website Behavior Analysis: URLScan provides information on the website’s behavior, such as JavaScript execution, network requests, and potential interaction with user inputs. This helps identify any suspicious or malicious activities.
- Security and Vulnerability Assessment: URLScan detects potential security risks by identifying known vulnerabilities or misconfigurations on the analyzed website. It can alert users to issues such as cross-site scripting (XSS), SQL injection, or insecure server configurations.
- Malware Detection: URLScan checks for indicators of malware on the website, including links to malicious files, known malicious domains, or suspicious URLs. This helps in identifying potential threats and protecting users from visiting compromised websites.
10. MXToolBox
MXToolbox is an online service that provides various tools and utilities to assist with the management and troubleshooting of email-related issues. It offers a range of features that help analyze and optimize email delivery, DNS records, and network configurations.
Here are some key features of MXToolbox:
- Email Deliverability Analysis: MXToolbox allows you to check the deliverability of your emails by performing various tests, such as SMTP connection tests, DNS-based Blackhole List (DNSBL) checks, and email header analysis. It helps identify potential issues that may affect email delivery to ensure optimal email communication.
- DNS Management: MXToolbox provides tools for analyzing and managing DNS records. It allows you to check DNS configurations, perform DNS lookups, verify DNSSEC signatures, and troubleshoot DNS-related issues.
- Blacklist Monitoring: MXToolbox helps monitor your IP addresses or domain names for presence on popular email blacklists. By regularly checking for blacklisting, you can take appropriate actions to address any reputation issues that may affect email deliverability.
- SPF, DKIM, and DMARC Analysis: MXToolbox assists with the analysis and validation of SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance) records. These protocols help authenticate and secure email communications, reducing the likelihood of spoofing and phishing attacks.
- SMTP Diagnostics: MXToolbox offers SMTP diagnostics tools to troubleshoot email delivery issues. It allows you to test SMTP connections, perform email server checks, and validate mail servers’ configurations.
- DNS and Network Monitoring: MXToolbox provides monitoring services to track the availability and performance of your DNS and network infrastructure. It helps identify and address potential issues proactively, ensuring smooth email operations.
- Reporting and Alerting: MXToolbox generates reports and alerts to keep you informed about the status and health of your email delivery and DNS infrastructure. It provides insights into performance metrics, blacklisting status, and any detected issues.
11. The Hive Project
TheHive is an open-source security incident response platform designed to help security teams manage and investigate security incidents effectively. It provides a centralized platform for collaboration, case management, and automation to streamline incident response processes.
Here are some key features of TheHive:
- Case Management: TheHive allows SOC teams to create and manage individual cases for security incidents. Each case acts as a container for related information, such as evidence, analysis, and response actions.
- Collaboration and Teamwork: TheHive supports collaboration among team members by enabling them to work on cases together. Users can assign tasks, leave comments, and share information within the platform, facilitating effective teamwork and knowledge sharing.
- Incident Triage and Analysis: TheHive helps SOC teams perform incident triage by collecting and organizing relevant information. It allows users to capture and analyze indicators of compromise (IOCs), log entries, and other data to gain insights into the nature and severity of incidents.
- Alert and Event Integration: TheHive integrates with various security tools and platforms to receive alerts and events, enabling automatic case creation and enrichment with contextual information. This helps expedite the incident response process.
- Playbooks and Automation: TheHive supports the creation and execution of automated response actions through customizable playbooks. Playbooks define a series of steps to be executed based on predefined triggers or conditions, enabling SOC teams to automate repetitive tasks and response actions.
- Reporting and Metrics: TheHive provides reporting capabilities, allowing SOC teams to generate customizable reports on incident metrics, response times, and key performance indicators (KPIs). This helps in measuring the effectiveness of incident response efforts.
- Integration Ecosystem: TheHive offers a wide range of integrations with popular security tools and platforms, such as SIEMs, threat intelligence feeds and Prowl, and ticketing systems. This allows for seamless data exchange and enrichment, enhancing the capabilities of the platform.
12. Wazuh
Wazuh is an open-source security monitoring and threat detection platform. It provides an extensive set of tools and capabilities to help organizations monitor their systems, detect security events, and respond to potential threats effectively.
Here are some key features of Wazuh:
- Log Management and Analysis: Wazuh collects and analyzes logs from various sources, including operating systems, applications, and network devices. It helps organizations gain visibility into their environments and identify security-related events and anomalies.
- Intrusion Detection: Wazuh includes an intrusion detection system (IDS) that detects suspicious activities and potential security breaches. It uses a combination of signature-based rules and anomaly detection to identify known and unknown threats.
- File Integrity Monitoring (FIM): Wazuh monitors the integrity of critical files and directories on systems. It alerts administrators when changes occur, helping to detect unauthorized modifications that could indicate a security compromise.
- Compliance Monitoring: Wazuh assists organizations in meeting regulatory and compliance requirements by providing predefined rules and policies for monitoring and reporting. It helps with compliance frameworks such as PCI-DSS, HIPAA, GDPR, and more.
- Vulnerability Detection: Wazuh integrates with vulnerability assessment tools, such as OpenVAS and Nessus, to correlate vulnerability scan results with security events. This helps prioritize remediation efforts and identify potential exploitation attempts.
13. Snare
Snare is a state-of-the-art Deception as a Service (DaaS) solution offered by Lupovis. It goes beyond traditional cybersecurity measures by strategically deploying decoys and traps to actively lure attackers away from valuable assets.
Price: Free 30-day trial, $2000/ mo per decoy for Premium, decreases with number of decoys deployed, or contact lupovis for quote.
This proactive approach helps eliminate false alarms and ensures that real threats are efficiently detected and mitigated. Snare provides real-time, contextual threat intelligence, enabling organizations to stay ahead of emerging threats and mount effective defenses. With Lupovis Snare, organizations can enhance their cybersecurity posture and gain a significant advantage in protecting their critical assets.
- Enhanced Detection: Lupovis Snare provides SOC teams with advanced deception techniques, allowing them to detect and identify attackers early in the cyber kill chain.
- Reduced False Alarms: By strategically deploying decoys and traps, Snare helps eliminate false alarms, enabling SOC teams to focus their resources on genuine threats and improve response efficiency.
- Proactive Defense: Snare’s active deception strategy allows SOC teams to proactively lure and divert attackers, disrupting their activities and minimizing the potential impact of cyber attacks.
- Real-time Threat Intelligence: Snare provides SOC teams with real-time, contextual threat intelligence, empowering them with up-to-date information to make informed decisions and respond effectively to emerging threats.
- Improved Incident Response: With its high-fidelity alerts and actionable insights, Snare enhances SOC teams’ incident response capabilities, enabling them to quickly and effectively mitigate threats and minimize the impact of security incidents.
- Enhanced Visibility: Lupovis Snare offers SOC teams a comprehensive view of adversary interactions, providing valuable insights into attack patterns, techniques, and potential vulnerabilities.
- Time and Resource Efficiency: By automating and streamlining threat detection and response processes, Snare helps SOC teams optimize their time and resources, allowing them to focus on critical tasks and efficiently address emerging threats.
- Threat Hunting Capabilities: Snare empowers SOC teams with the ability to actively hunt for threats within their networks, enabling proactive identification and mitigation of potential risks before they escalate.
- Continuous Improvement: Lupovis Snare leverages machine learning and AI algorithms to continuously adapt and improve its deception techniques, staying one step ahead of evolving attacker tactics and ensuring ongoing effectiveness.
- Cost Savings: By reducing false positives and minimizing incident response times, Snare helps SOC teams save on operational costs associated with investigating and addressing non-malicious activities, enabling more efficient resource allocation.
4 July 2023 | by Xavier Bellekens
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.


