Security Against Mass Exploitation
✅ Identify mass exploit activity associated to your attack surface. ✅ IP blocklists to prioritize patching. ✅ Block mass attack IPs directly at the perimeter
Accelerate Triage
✅ Identify malicious IP and reduce triage time ✅ Obtain context on IPs intentions ✅ Automate workflows and filter the noise for SIEM, SOAR and other tools.
Threat Hunting Automation
✅ Assist threat hunters in identifying the methods and strategies used by attackers using attack data. ✅ Enhance and automate current cyber threat research using IP information. ✅ Enrich IP information in your SIEM

Actionable IP context
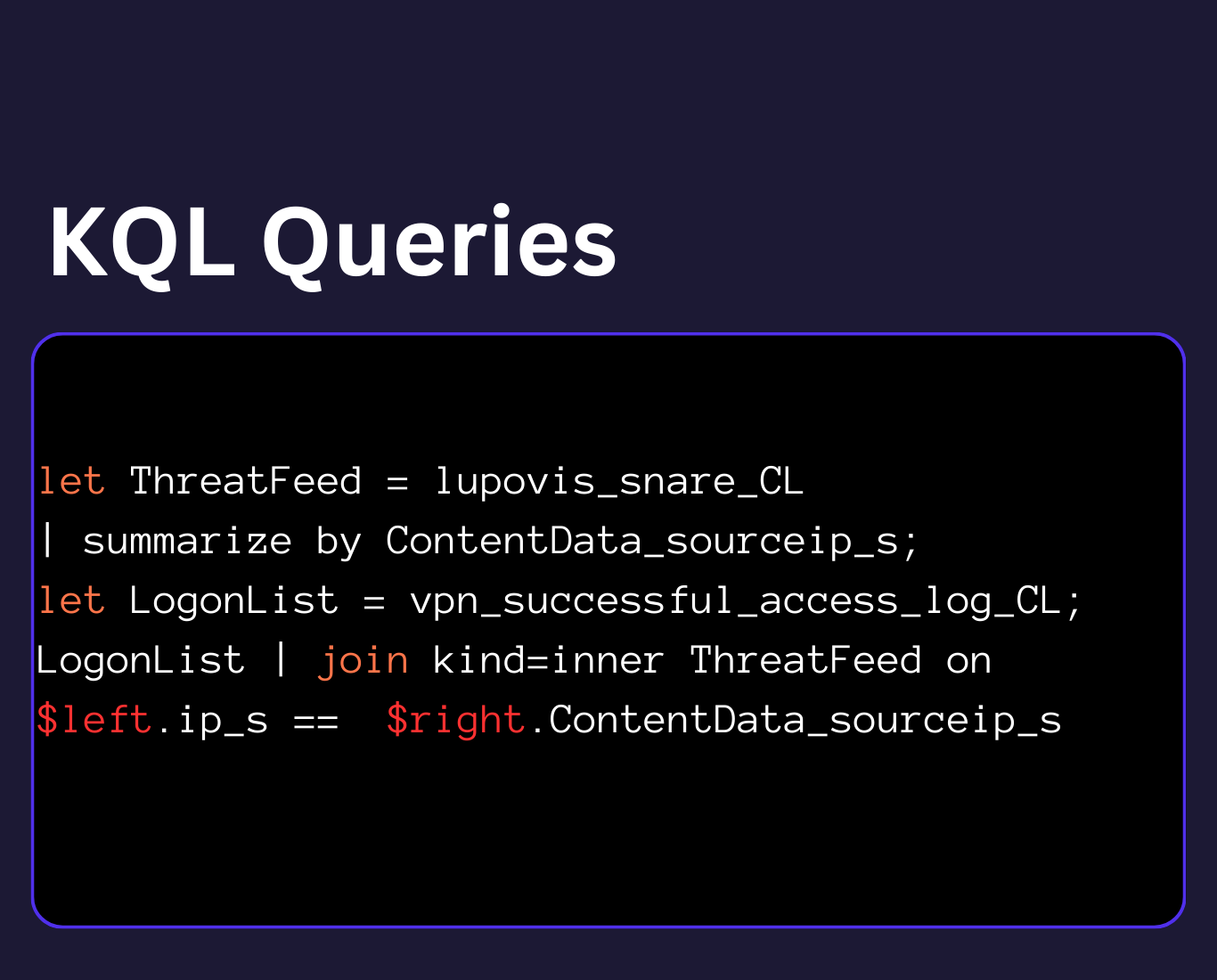
No more worries about mass alerts! Lupovis Prowl CTI aggregates data and information for you, and shares it through an API, enabling your SOC team to spend less time on irrelevant activities, and boosting the operation’s efficiency.
Aggregate
Our sensor collects internet activity and attack traffic.
Analyze
Our analytics engine automates enrichment and categorize the activity while providing context. We also identify and differentiate humans from bots activity.
Share
We share contextual, timely intelligence via our API and our web community interface
IT Manager in Healthcare
“After using Prowl for several weeks, I can confidently say that it is a great tool for understanding the traffic on our infrastructure and improving our SIEM triage times”
SOC Manager
“Lupovis helped identify humans, scanners and indicators of attacks associated with IPs. Prowl helped save time, avoiding our analysts going down rabbit holes and automate playbooks.” “
MSSP Business Development Manager
“Our analysts use Prowl to enrich alerts coming through the SOC and quickly identify threats and benign traffic”