Automate IP addresses Enrichment in Azure Sentinel
19 December 2022 | by Xavier Bellekens
What is Azure Sentinel
Azure Sentinel is a cloud-native security information and event management (SIEM) solution. It provides threat protection, cybersecurity analytics, and automation to help organizations identify behavioral anomalies and investigate, detect, and respond to threats.
Azure Sentinel provides a central location to gather security data from across the organization, this data then has Sentinels insights layered on top of it – helping organizations reduce the time needed to investigate alerts.

What is IP enrichment?
IP enrichment makes use of third party integrations to add additional details about ‘who’ has been connecting to your services. These details are normally things such as geographical provenance, past cyberattacks associated with the address, or it’s aggressiveness.
With this data, businesses can gain insight into user trends and actions tied to the IP address and determine if the IP address is malicious or not. These actionable insights help provide additional data points to cybersecurity analysts to make decisions on whether to allow or deny access to that IP address.
Lupovis Prowl is an API that can be used to enrich IP data in an automated fashion, this is backed by a custom implementation of the Snare platform, which allows gathering of data on a massive amount of threat actors globally.
Once the data has been enriched, the insights acquired offer valuable intelligence for any organization wanting to stay updated on user actions or vigilant against adversaries or intruders. The higher fidelity enrichment provides can make a huge difference when applying automation, particularly in a Security Orchestration, Automation, and Response (SOAR) context.
Scenario with SIEM Integration
Lupovis is integrated directly into a SIEM where external IP addresses are automatically sent to the Lupovis Prowl API to enrich the data and help determine if the address is malicious or not.
Obtain an API Key
To obtain an API key you can visit the Amazon AWS Marketplace and subscribe to our API.
https://aws.amazon.com/marketplace/pp/prodview-cr64x4lse5uui
You will be able to make as many request on the API as needed for $0.02 cents per request.
Once subscribed, you will receive an email with the base URL of the API and the API key.
How To Use the API with Sentinel
Let’s take a simple example with a single host being enrolled in a ‘log analytics workspace’, once the device is enrolled, the device will begin sending heartbeats into the platform, along with syslog. Although we have a single instance here, this can be replicated with all infrastructure as needed to provide right size protection.
The query below shows the device that has been enrolled.
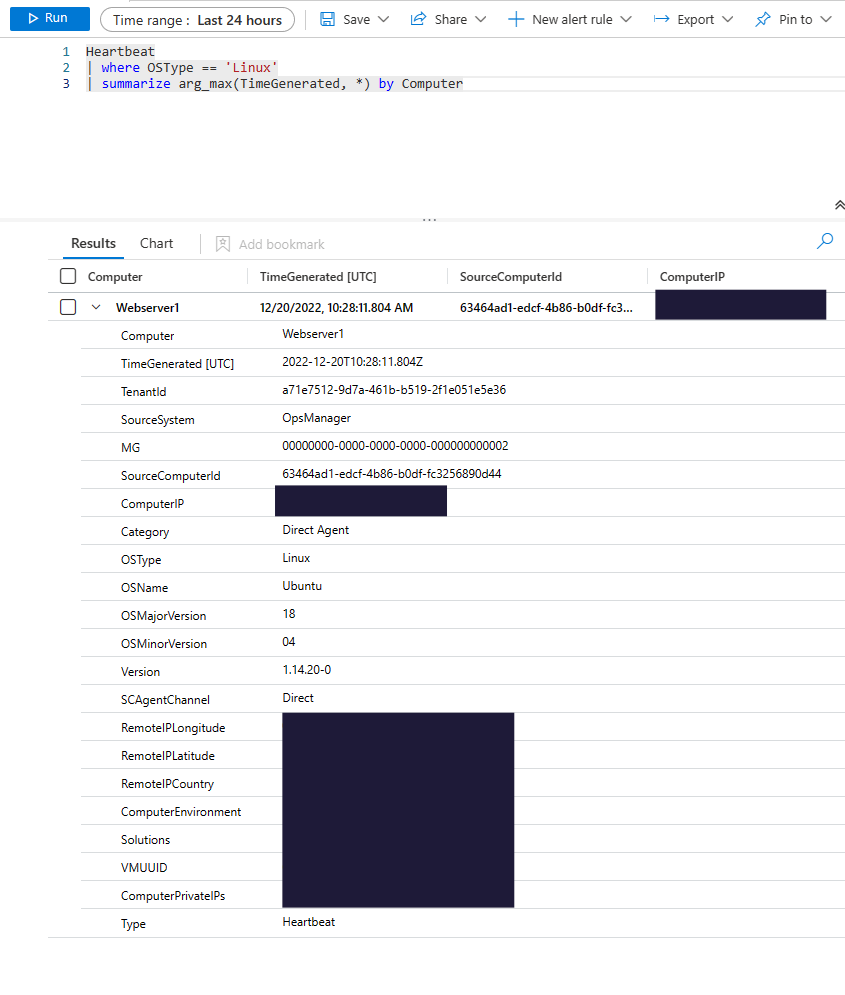
As we can see, our webserver1 was successfully added to the ‘log analytics workspace’, which is now receiving logs from the server. This will include all the events generated by syslog, in this example, we will be focused on login attempts.
We can verify this and pull out key information by using the following query.
Syslog
| where SyslogMessage startswith "Failed Password"
| order by EventTime desc
| extend User = extract("for(?s)(.*)from",1,SyslogMessage)
| extend IP = extract("(([0-9]{1,3})\\.([0-9]{1,3})\\.([0-9]{1,3})\\.(([0-9]{1,3})))",1,SyslogMessage)
| project HostName, SyslogMessage, EventTime, IP, User
Which outputs the following information
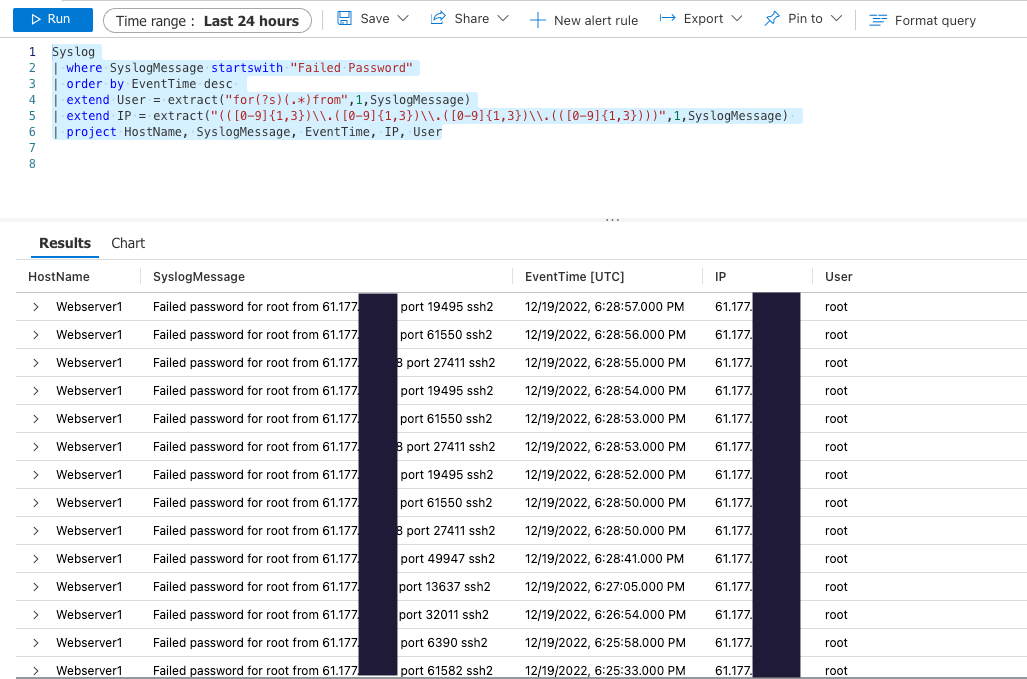
The 2nd and 4th column contain the IP addresses of the malicious adversary, in this case performing an SSH bruteforce on the “root” user. Note, that in this case, we have very little context for threat hunting on this given IP address.
As an analyst, it’s hard to label this IP addresses as noise, humans, or understand the Indicators of Attacks and Indicators of Compromise associated with the IP data obtained though syslog.
Note: any log with IP data can be enriched via the API request. Hence, the next step is to create an alert rule in Azure Sentinel that reads all syslog messages, extracts the IPs and removes the duplicates every 10 minutes – this can replaced with any alert rule you prefer, an example could be multiple failed login attempts to a VPN.

This alert rule will create an incident, which will then run the playbook and do the IP enrichment. The results of the IP enrichment will then be fed back into Azure Sentinel to provide data and context to the analyst. Further automation could also be built from this, an example could be if there has been multiple failed login attempts and the context from the enriched data shows this as a known attacker, block the connections.
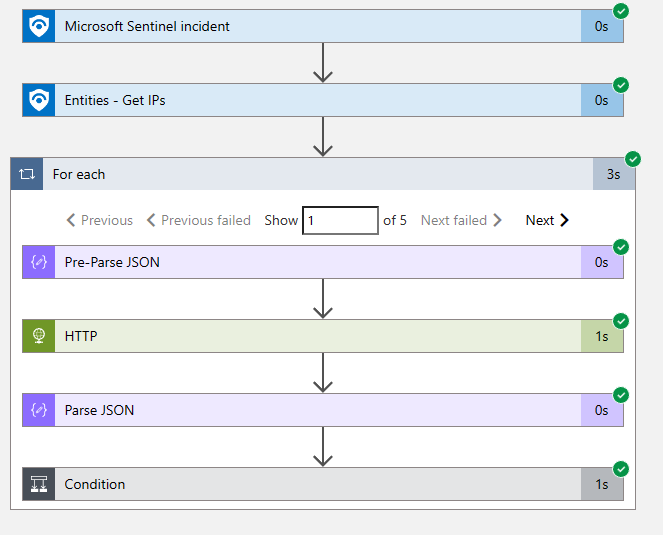
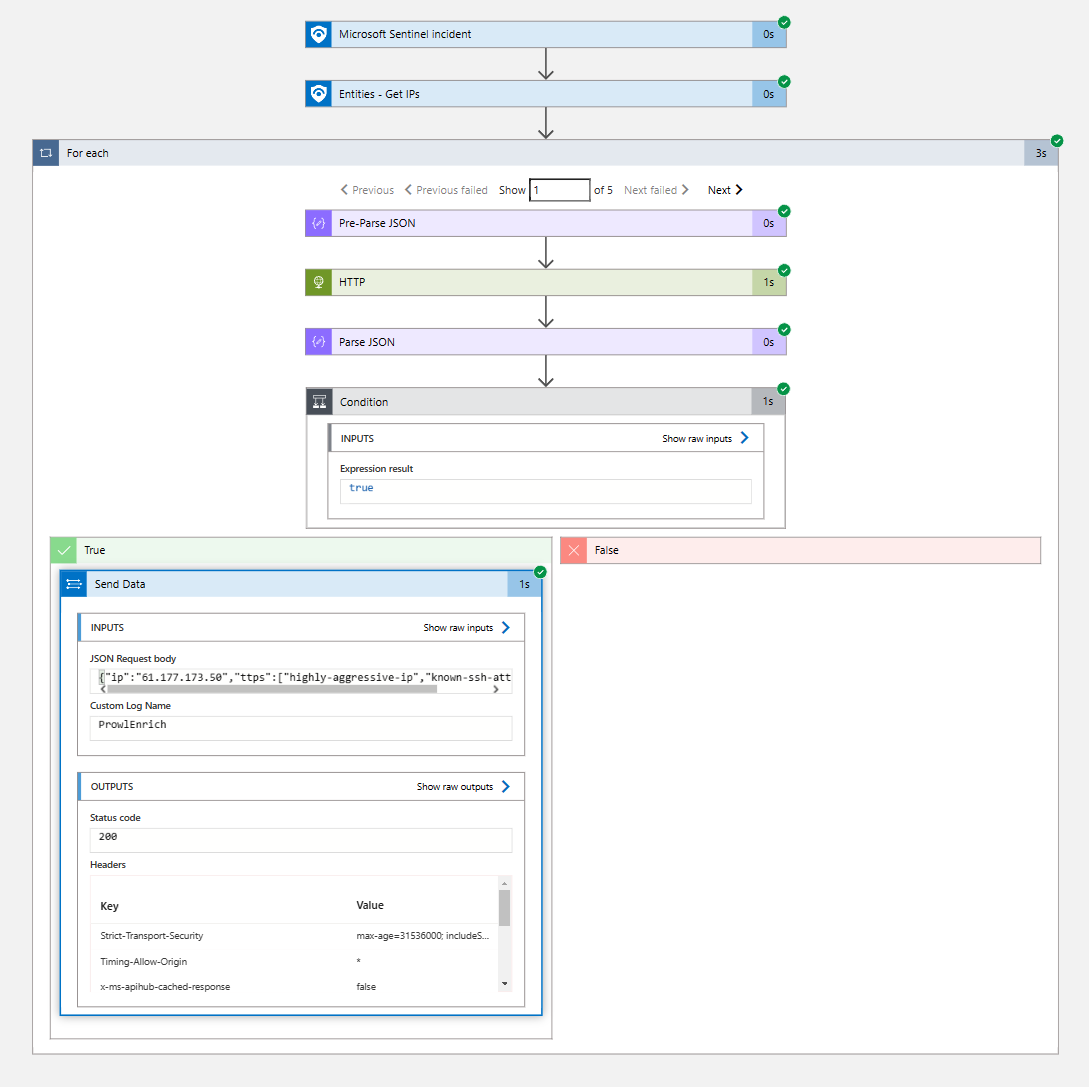
The Playbook
In this example, we created a Sentinel Automation Rule with the following core logic:
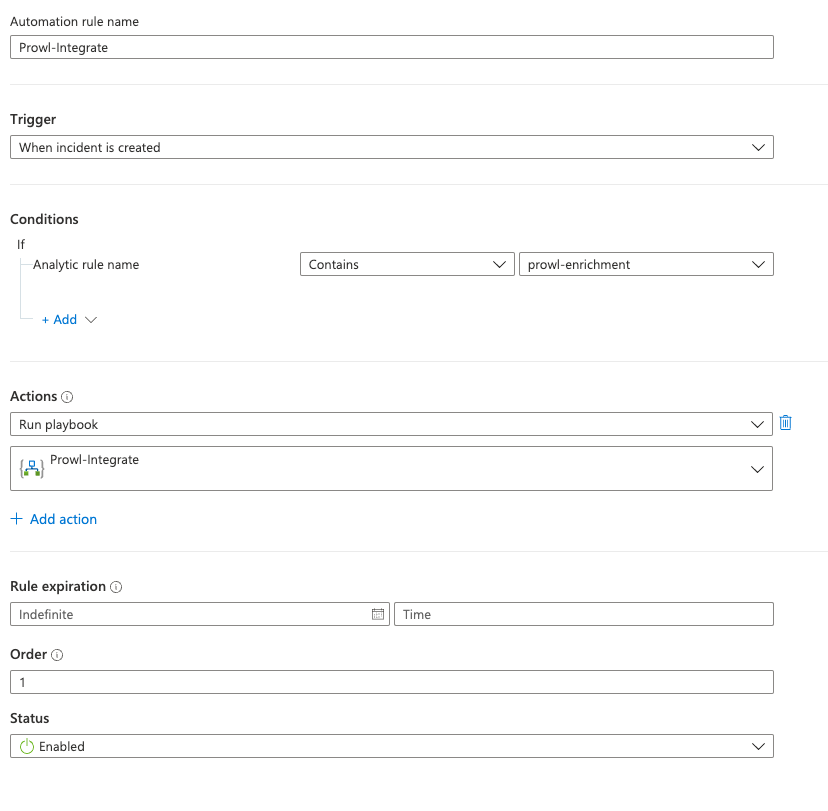
The rule creates the incident, which in turn makes sure that the playbook is executed periodically.
The playbook itself contains the following main steps:
- All the IPs are fetched from the incident

- For each IP we carry out an HTTP GET request against the Prowl API containing the IP address and the key for Prowl.
- All information, including tactics, techniques and procedures (TTPs) are returned in JSON format and then parsed. Included in the TTPs are what Lupovis call ‘Indicator of Intelligence’ which are our method of separating motivated human attackers and bots.
- The parsed results are written back to sentinel with a custom log name called ProwlEnrich

The Result
For each IP address coming through the logs, regardless if it’s someone performing a legitimate access or trying anything nefarious at the periphery of our network, the IP address is enriched with contextual information.
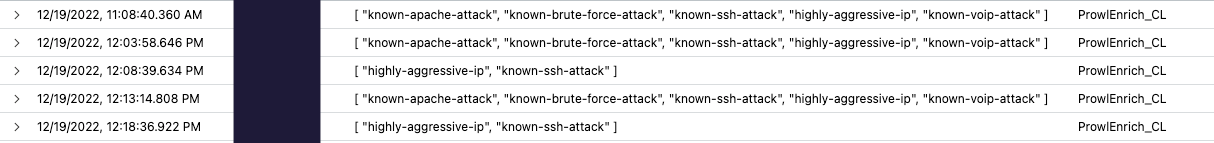
This IP lookup can help analysts and network administrators determine if someone is targeting the organization, create better report on the threats seen and the TTPs associated with the IP addresses and their reputation as well as remove the noise from the logs, identify leads faster and block & tag abusive IP addresses to focus on what matters.
19 December 2022 | by Xavier Bellekens
Speak to an Expert
Whether you have a specific security issue or are looking for more information on our Deception as a Service platform, simply request a call back with one of our security experts, at a time that suits you.